Malware analysis tools
Best malware analysis tools and their features.
Malware has
become a huge threat to organizations across the globe. Something as simple as
opening an email attachment can end up costing a company millions of dollars if
the appropriate controls are not in place. Thankfully, there are a plethora of
malware analysis tools to help curb these cyber threats.
When
responding to a security
incident involving malware, a digital forensics or research team will typically
gather and analyze a sample to better understand its capabilities and guide
their investigation.
There are a number of tools that can help security analysts reverse engineer malware samples. The good news is that a few malware analysis tools are completely free and open source.
1.peStudio
This is an
excellent tool for conducting an initial triage of a malware sample and allows
me to quickly pull out any suspicious artifacts.
Once a
binary has been loaded it will quickly provide the user with hashes of the
malware and any detections found in VirusTotal. A list of strings is also
pulled however if the sample is packed this may not return any strong IOCs,
unpacking the sample, and then reviewing the strings will often provide useful
information such as malicious domains and IP addresses.
The
screenshot above also shows the ‘entropy’ of the malware. This helps identify
whether the malware is packed or not. When a sample is packed this means the
malware author has effectively put a layer of code around the malware in order
to obfuscate its true functionality and prevent analysis of the malware.
To assist
with identifying packed malware PeStudio displays the level of entropy of the
file. Entropy is measured on a scale of 0-8, with 8 being the highest level of
entropy. The higher the entropy the more likely that a piece of malware is
packed.
Another
useful section is the ‘Imports’ tab, this contains functionality that is
imported into the malware so it can perform certain tasks. For example, Windows
contains various libraries called DLLs, this stands for dynamic link library.
Each library contains a unique set of functions known as Windows APIs, these
are used by legitimate programs to perform various functions. For example, the
DLL Kerner32.dll contains the API CreateProcessW, this can be used by a piece
of software to create a new running process. However, malware will use the same
methodology to import its own functionality. If the malware needs to create a
new file on disk, the malware author doesn’t need to write a piece of code to
do that they can just import the API CreateFileW into the malware. By looking
at the imports a malware analyst may be able to predict the potential behavior
of the malware.
Link :- https://www.winitor.com/download
2. Process
Hacker
Process
Hacker allows a malware analyst to see what processes are running on a device.
This can be useful when detonating a piece of malware to see what new processes
are created by the malware and where these are being run from on disk. Malware
will often try to hide by copying itself to a new location and then renaming
itself, Process Hacker will display this activity occurring making it easy to
identify how the malware is attempting to hide.
Link :- https://processhacker.sourceforge.io/
3. Process Monitor(ProcMon)
ProcMon is a
powerful tool from Microsoft which records live filesystem activity such as
process creations and registry changes. This is really handy when used in
tandem with Process Hacker as a new process may be created and then quickly
killed, this process can then be reviewed in the ProcMon capture.
One issue
with ProcMon is that in a matter of seconds it can quickly record over 100,000
events. Although the filters in ProcMon are excellent there is always a risk an
event of interest could be missed, however, this data can be exported as a CSV
and imported into the next tool in my list.
Link :- https://learn.microsoft.com/en-us/sysinternals/downloads/procmon
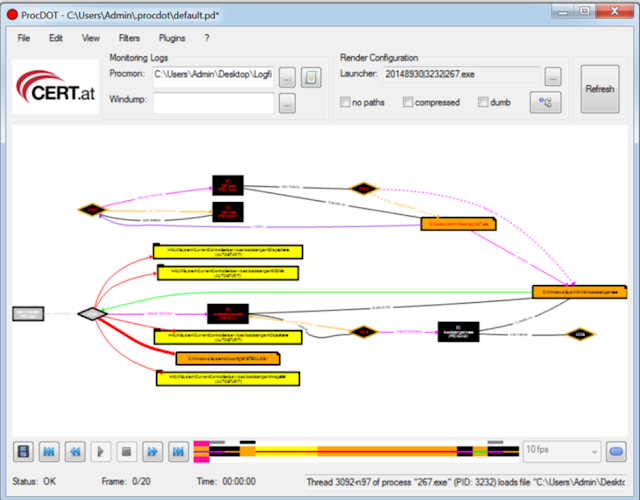
4. ProcDot
ProcDot allows a malware analyst to ingest the output from ProcMon
and automatically generate a graphical representation of the captured data.
Simply upload the csv into ProcDot and select the process name of the malware.
Rather than creating filters and navigating hundreds of thousands of events you
are now able to navigate a visual diagram of what recorded malware activity.
Link :- https://www.procdot.com
5. Autoruns
Autoruns is another Microsoft tool that will display any installed software on a device that is set to launch when a machine is powered on. Malware can hide but ultimately it has to run and in order to survive a reboot a piece of malware must create a persistence mechanism.
There are a few techniques that can be employed to achieve this
objective such as creating a scheduled task or creating specific run keys
within the registry. After running a piece of malware in a VM running Autoruns
will detect and highlight any new persistent software and the technique it has
implemented making it ideal for malware analysis.
Link :- https://learn.microsoft.com/en-us/sysinternals/downloads/autoruns
7. Wireshark
Wireshark is
the de facto tool for capturing and analysing network traffic. Whereas a web
proxy such as Fiddler is focused on HTTP/HTTPS traffic, Wireshark allows deep
packet inspection of multiple protocols at multiple layers. While analysing
packet captures in Wireshark it is even possible to extract files from the pcap
that have been downloaded by the malware.
Link :- https://www.wireshark.org/
8. x64dbg
This tool is
for manually debugging and reverse engineering malware samples, you need to have an understanding of assembly
code to use this tool however once that learning curve has plateaued it allows
a malware analyst to manually unpack and take apart malware samples like a
surgeon with a scalpel.
Understanding
how to use x64dbg means you can focus on specific functions and imported API
calls of a sample and begin to dissect how the malware truly operates.
Link :- https://sourceforge.net/projects/x64dbg/
9. Ghidra
Ghidra was
developed by the National Security Agency (NSA) and is what’s known as a
disassembler rather than a debugger. Using Ghidra you are able to navigate the
assembly code functions like in x64dbg, however, the key difference is that the
code is not executed, it is disassembled so that it can be statically analyzed.
Another key
difference from x64dbg is that Ghidra will attempt to decompile the code into a
human-readable output that is close to what the malware author will have
written when creating the malware. This can often make it easier for a malware
analyst to reverse engineer the malware as they are presented with the
variables and instructions which make up each function.
10. Radare2/cutter
Radare2 is a
command-line debugger that can be used on Windows and Linux, what I really like
about Radare2 is that unlike x64dbg it has the capability to analyze Linux
executables. To make Radare2 more user-friendly for those who may be put off by
the command line interface. It also has a GUI front end known as Cutter.
Link :- https://rada.re/n/radare2.html
11. Resource
Hacker
Resource
Hacker™ is a resource editor for 32bit and 64bit Windows® applications. It's
both a resource compiler (for *.rc files), and a decompiler - enabling viewing
and editing of resources in executables (*.exe; *.dll; *.scr; etc) and compiled
resource libraries (*.res, *.mui). While Resource Hacker™ is primarily a GUI
application, it also provides many options for compiling and decompiling
resources from the command-line.
Link :- http://www.angusj.com/resourcehacker/#download
12 .
signsrch.exe
this tool
for searching signatures inside files, extremely useful in reversing
engineering for figuring or having an initial idea of what
encryption/compression algorithm is used for a proprietary protocol or file.
it can
recognize tons of compression, multimedia and encryption algorithms and many
other things like known strings and anti-debugging code which can be also
manually added since it's all based on a text signature file read at runtime
and easy to modify.
supports
multithreading, scanning of folders using wildcards, scanning of processes,
conversion of the executables offsets in memory offsets, loading of custom
signature files and their automatic checking for avoiding errors, automatic
finding of the instructions that reference the found signatures (like
"Find references" of Ollydbg) and the launching of an executable
placing an INT3 byte at the desired memory offset (for example one of those
retrieved with the -F option, watch the Video setion for an example).
the tool
supports 8, 16, 32 and 64 bits, float and double plus automatic CRC table
creation and C style strings.
Link :- http://aluigi.altervista.org/mytoolz.htm
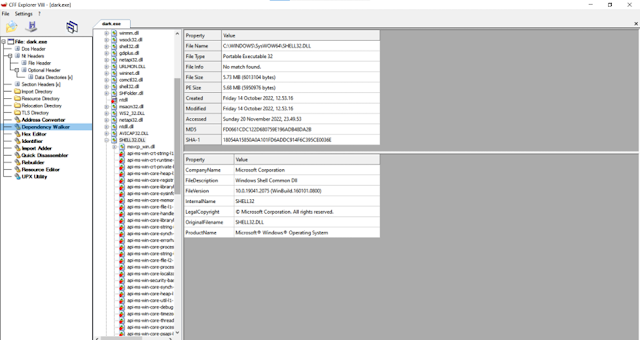
13. CFF
Explorer
CFF Explorer
was designed to make PE editing as easy as possible, but without losing sight
on the portable executable’s internal structure. This application includes a
series of tools which might help not only reverse engineers but also
programmers. It offers a multi-file environment and a switchable interface.
Link :- https://ntcore.com/
Watches for
the CMD, PowerShell and other processes, suspends it, extracts the command line
data, then optionally kills it. There's also an interactive mode to handle any
LOLBin. This tool enables you to quickly obtain deobfuscated output from VBA
macros. This is a single, portable executable (32 and 64-bit versions) that
requires .NET
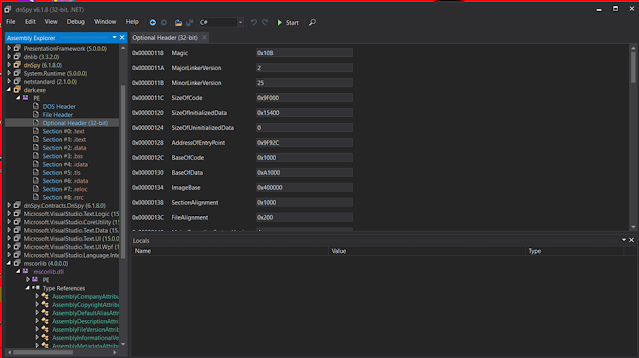
15 . dnSpy
dnSpy is a
debugger and .NET assembly editor. You can use it to edit and debug assemblies
even if you don't have any source code available.
Main
features:
◉Debug .NET and Unity assemblies
◉Edit .NET and Unity assemblies
Link :- https://github.com/dnSpy/dnSpy/releases
16. PE-bear
PE-bear is a
freeware, multi-platform reversing tool for PE files, based on bearparser
(license) & capstone (license). Its objective is to deliver fast and
flexible “first view” for malware analysts, stable and capable to handle
malformed PE files.
Link :- https://github.com/hasherezade/pe-bear/releases/
17. IDA
IDA(Interactive
Disassembler Professional) is a disassembler for computer software which generates
assembly language source code from machine-executable code. It supports a
variety of executable formats for different processors and operating systems.
It also can be used as a debugger for Windows PE, Mac OS X Mach-O and Linux ELF
executables. A decompiler plug-in for programs compiled with a C/C++ compiler
is available at extra cost. The latest full version of IDA Pro is commercial;
while an earlier and less capable version is available for download free of
charge
IDA performs
automatic code analysis, using cross-references between code sections,
knowledge of parameters of API calls, and other information. However, the
nature of disassembly precludes total accuracy, and a great deal of human
intervention is necessarily required; IDA has interactive functionality to aid
in improving the disassembly. A typical IDA user will begin with an
automatically generated disassembly listing and then convert sections from code
to data and vice versa, rename, annotate, and otherwise add information to the
listing, until it becomes clear what it does.
Link :- https://github.com/AngelKitty/IDA7.0
VirusTotal
was founded in 2004 as a free service that analyzes files and URLs for viruses,
worms, trojans and other kinds of malicious content. Our goal is to make the
internet a safer place through collaboration between members of the antivirus
industry, researchers and end users of all kinds.
Link :- https://www.virustotal.com/gui/home/upload
19. hybrid
analysis
This is a
free malware analysis service for the community that detects and analyzes
unknown threats using a unique Hybrid Analysis technology.
Link :- https://hybrid-analysis.com/
20. any.run
ANY.RUN
sandbox is a malware hunting service that benefits education goals. It
perfectly blends with the training process. There is no need to teach students
how to use it – the interface is simple enough for beginners. Plenty of
real-time information for analysis and monitoring samples’ malicious behavior
guarantees a profound basis for learning.
The
interactive sandbox is convenient for learning:
◉ See the analysis results right away,
how malware executes, and it doesn’t require any preparation. Just start the
task and get the result.
◉ A user-friendly interface allows performing effective and
qualitative investigations even for junior specialists.
◉ A huge database of samples and IOCs.
◉ The unlimited number of tasks.
◉ Detailed reports will help you find the necessary information
quickly and export it.
◉ Work together on one sample. Create a team and track each
member’s activity.
Link :- https://any.run/
21. unpac.me
UNPACME is
an automated malware unpacking service. Submissions to UNPACME are analyzed
using a set of custom unpacking and artifact extraction processes. These
processes extract all encrypted or packed payloads from the submission and
return a unique set of payloads to the user. In short, UNPACME automates the
first step in your malware analysis process.
Link :- https://www.unpac.me/#/
22. tria.ge
Triage is a
fully automated solution for high-volume malware analysis using advanced
sandboxing technology.
Link :- https://tria.ge/dashboard
23 . Yomi by
yoroi
the Malware Hunter is a free sandbox-based file analysis service. From the submission interface, you can analyze files for detecting malicious behaviours and suspicious characteristics.
Yomi is completely hosted in Italy and actively maintained by Italian developers and analysts. We released Yomi Hunter to help the security community against cyber criminals, while we can use your feedback to improve our detection and defence capabilities.
Link :- https://yomi.yoroi.company
24. Intezer
analyze
Intezer automates alert triage,
incident response and threat hunting by analyzing potential threats (such as
files, URLs, endpoints) and automatically extracts IoCs/hunting rules—providing
clear classification and better detection opportunities. Easily integrates into
SOC and IR teams workflows (EDR, SOAR, SIEM, etc.) to eliminate most false
positives and reduce 90% of alert response time.
Link:- https://analyze.intezer.com/
























Great article thank you for sharing the valuable information with us.
ReplyDeleteBest Cybersecurity Services.